
As a network security practitioner, your job is to protect your company from threats, which can come from hackers outside your network or employees within your network. In this article, I will cover 10 practical tips you can apply today to improve your network security and protect your network from threats.
Tip 1: Manage Your Passwords
Passwords are everywhere and the results are in - people are the weakest link when it comes to problems with passwords. Providing users with a way of managing their passwords can go a long way to improving your network security. Start by providing a password manager - there are many free and paid password managers on the market. To name a few, Okta, 1Password, Keeper, LastPass, and KeePass. These tools allow users to save passwords in a secure vault, so they no longer need to remember them or store them in the browser. Most password managers have capability that will automatically fill username and password details for users, which is a great convenience. Good password managers have a password generator built in that generate high-entropy (long and complex) passwords that your users don't even need to know.
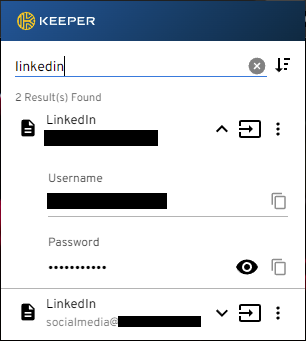
I have personally been using Keeper since 2014 and love it. It stores my passwords using strong encryption and is easy to use. When I need a password, I can search for it, or the browser plugin will recognize I am logging into a site and fill my username and password for me automatically. The screenshot below shows a search for my LinkedIn accounts in the Keeper browser plugin.
With a password manager in your users' hands, the next step for managing your passwords is to tighten the bolts on password policies. It is good security practice to enforce minimum password complexity requirements wherever possible. Passwords should be required to adhere to at least the following characteristics:
- Password length is at least 12 characters
- Password contains a mix of uppercase and lowercase characters
- Password contains at least one number
- Password contains at least one non-alphanumeric character (special characters)
- Password does not contain repeating characters
- Password does not contain a sequence of adjacent digits (e.g., 1234)
- Password must be changed at least once every 90 days
Perform an audit of the password policies for all the business applications used in your organization and bump up the complexity requirements wherever you can. Of course, this is easier if you have given your users a password manager since the change in complexity requirements will not result in an increased support burden for lockouts and resets.
The last thing I will mention in this tip is that passwords are the way of the past. Increasingly, application developers are shifting to using federated authentication technologies that avoid passwords altogether. Authentication and authorization schemes such as SAML, OpenID Connect, OAuth 2.0, and LDAP are becoming the norm, especially in cloud applications built with a Software-as-a-Service (SaaS) model. It is highly advisable to use federated authentication schemes whenever possible, as they avoid using passwords altogether and help protect your network from hackers. Most password managers support these schemes.
Tip 2: Update Software
Keeping software up to date across your network is a great way to protect your network from hackers. Software vendors release frequent updates that include bug fixes, security patches, and improvements to the user experience. Be sure that all devices across your network are kept up to date to prevent holes in the software from being exploited. The devices you should keep up to date with patches on your network are servers, end-user devices such as workstations, laptops, and mobile phones, routers, firewalls, and printers. The software you should keep up to date with patches on your network are operating systems, browsers, third-party software, plugins, and extensions.
As you maintain your network, be on the lookout for vulnerabilities disclosed by your vendors, as well as the recommend patches, workarounds, and other protective measures. A zero-day attack is an unpatched vulnerability in a system that can be exploited and cause damage to your organization. It is essential to mitigate these vulnerabilities before attackers have a chance to exploit them. Staying on top of patching and making it a part of a regular cycle of system maintenance goes a long way toward closing security holes and preventing attacks. If you have an in-house software and a development team, be sure to communicate news of any recent vulnerabilities and their severity to them.
Tip 3: Train Users to Avoid Links
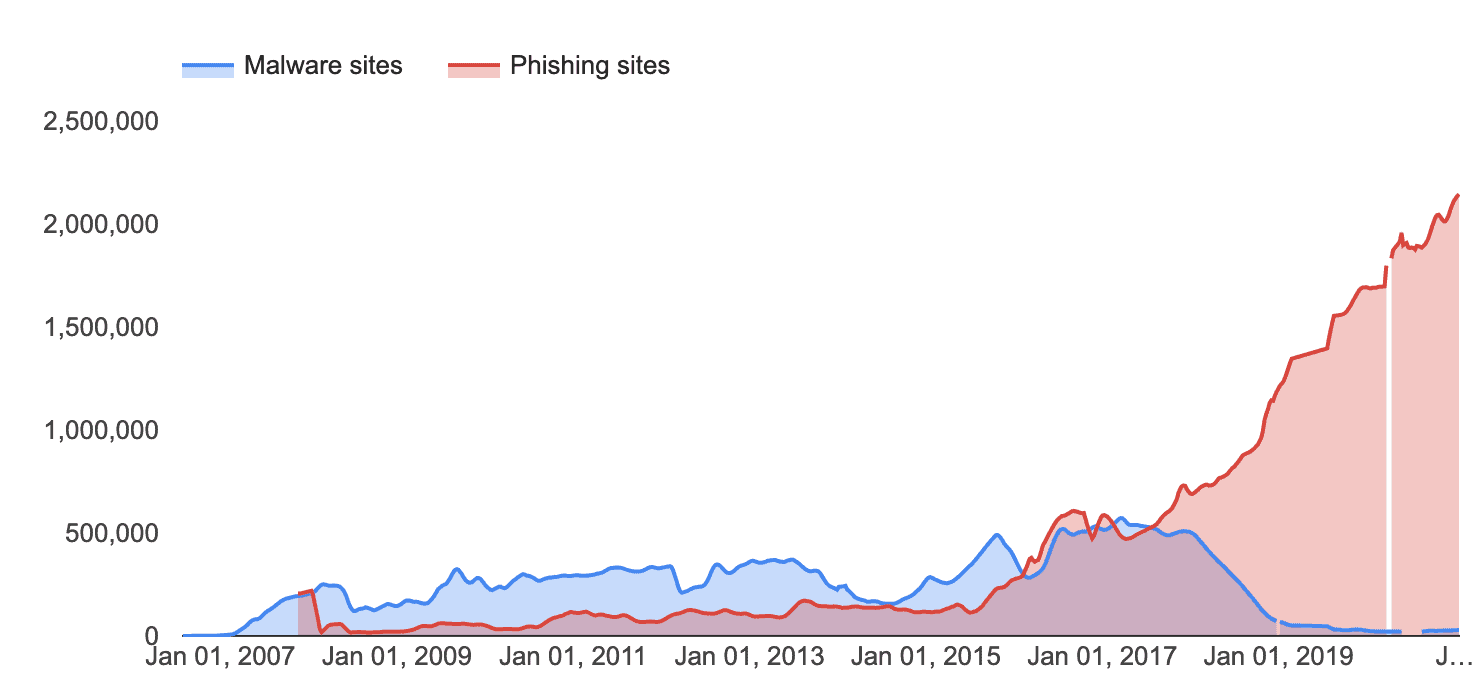
We all love email, right? Some of us do and some of us don't, but you can't escape the fact that much of business today relies on email. Email is an information service that virtually every user in an organization uses, so it's not surprising that email is a frequent (and surprisingly vulnerable) target of attack. The number of phishing sites has surpassed the number of malware sites in recent years, as you can see from the chart below:
A phishing attack works by sending a link to a user, frequently disguised as a legitimate message, or coming from a legitimate source and getting the user to click on the link so they download malware, command and control executables, or provide their network credentials in a web form. These attacks are known as malware delivery, command and control, and credential harvesting, respectively. One frequent approach attackers use is spoofing, where the attacker purports to be somebody the recipient knows, such as the CEO or CFO. Use SPF on your email domain to authorize external servers and senders and an email filtering service to prevent users form ever receiving spoofed messages.
To protect your network, your employees, and your organization, here are a few general principles you can follow and train your users to follow:
- Never click links or open attachments from unknown senders.
- Even if you know the sender, only click links or open attachments if you were expecting them.
- Hover over all links to display the URL *before *clicking and verify that it appears legitimate.
- Train users to be alert to potential malicious emails and report them when they see them.
- Train IT staff to respond to suspected phishing submissions in a timely manner and provide meaningful feedback to users.
Tip 4: Embrace the Principle of Least Privilege
The principle of least privilege is the security concept that any user, administrator, system, or software should have only the minimum permissions required to perform its function and no more. This approach can be unpopular for users, but it is an essential step to protecting your network form hackers. Giving users only the necessary permissions to perform their jobs protects against unintended system changes that could expose vulnerabilities, accidental changes, and - in the event of an attack - reduces the ease with which hackers can escalate privileges and do damage to your network, data, and organizational reputation.
The principle of least privilege is a simple one, but it should not be taken for granted. Administrators should also play by the same restrictive rules. A good practice for system administrators to follow is to use two accounts, one for their day-to-day work that has no more privileges on the network than a typical user, and one for doing administrative work as needed. The same principles for managing passwords in Tip #1 above apply here. Where possible, password policies for administrative accounts should be higher than for typical users and multi-factor authentication (MFA) should be used on all administrative interfaces.
Tip 5: Use Strong Encryption
Encryption is a vital part of the Internet and there is good reason for this. Encryption helps keep our data safe from hackers and has been used for decades to secure sensitive information, such as credit card numbers. With massive data breaches, like the recent GoDaddy breach, attackers are creating serious problems across many fields. It is becoming imperative to use strong encryption and other measures to keep your network and domain secure.
As a web developer, DevOps team, IT support, or everyday user of the Internet, you need to be aware of the encryption used by the sites you host and the sites you visit. Here are a few general principles I have for using strong encryption:
- Do not use sites without encryption support for TLS 1.2 or higher.
- Always make sure sites you visit show a lock symbol and
https://in the address bar. - Monitor your domain for expiring certificates. You can use NetworkCalc's certificate tool to ensure your certificate is valid.
- Check your website security regularly using a tool like Qualys SSL Labs.
- Use HTTP Strict Transport Security (HSTS) on your websites to protect against man-in-the-middle attacks.
- Remove support for weak ciphers on your web servers, including RC4 and ciphers with a key length less that 1024 bits.
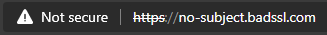
Most modern web browsers will show some visual indicator of an unencrypted site like the one shown below from Microsoft Edge. Be on the lookout for signs of a site not using strong encryption and steer clear of it.
Use the security tools below to look up your website's certificate and ensure that you are using strong encryption.
Security Tools
Tip 6: Install Anti-Virus Software
This one is a simple tip - to protect systems from infection, install anti-virus software, ensure that it receives regular software updates and version updates, and schedule anti-virus scans to run on a schedule, on demand, and on file access. Protecting systems from infection is a top priority in any network security program. When it comes to ensuring computers are safe from malware, anti-virus software provides a good layer of protection on the endpoint.
There are several free anti-virus scanners available that have certain limitations, as well many commercially available, off-the-shelf ones. Whether you manage a single computer or a fleet of thousands, make sure all your endpoints are protected and stay up to date. Zero-day vulnerabilities can be exploited fast (within days or hours), so automating updates to your anti-virus software will help ensure you have the vendor's latest signature updates to identify and protect against new vulnerabilities in the wild.
In addition to the anti-virus software installed on your machines, stay alert to major vulnerabilities disclosed in vendor publications. Be aware of risks in second-party software (operating systems), third-party software (from software vendors), and fourth-party software (from vendors of software vendors) at a minimum.
Tip 7: Encrypt Your Backups
Backups are an essential part of disaster recovery, and you should make sure they are encrypted. Unencrypted backups are vulnerable to information disclosure. If an attacker got their hands on your backups and they were unencrypted, the attacked would have access to your valuable data and any personal information stored within the backups. For this reason, it is important to encrypt your backups and store physical backup media in a secured location.
As a general principle when dealing with company data, you should look for ways to encrypt and secure data in all its states: at rest, in transit, and in use. The best way to protect data is by looking for ways that data can be encrypted while users are accessing the data, while the data are being transmitted or received, and while data are sitting in storage, including in backups.
Tip 8: Disable or Harden Sharing Services
It is often said that sharing is caring but sharing services on a network-connected device are a frequent source of vulnerability. Sharing and printing services should be turned off whenever possible, since they are very easy targets for attackers.
A good principle for thinking about network security is this: if a network service or level of access is not absolutely required, it should be turned off, disabled, or hardened. This applies equally well in the contexts of least permissions and network services. If a service or access level is not strictly required, it is a good practice to disable it. If a service or access level is required, be sure you take the time to configure it to be as secure as you can without complete loss of functionality. I understand sharing services are sometimes required, so when they are, be sure to harden them by evaluating security settings and user access permissions to achieve least privilege access.
Among the sharing services to consider when looking into your network security are file sharing, printer sharing, collaboration software, and location sharing.
Tip 9: Change Default Passwords and SSIDs
Network equipment like firewalls, routers, switches, and access points are shipped with default configuration, including default passwords, default networks, and default SSIDs. It is tempting to jump in and start configuring network devices, creating rules, copying config, and testing capabilities. Before jumping into the fun stuff, it is a good idea to take care of one of the basic tenets of network security: change the default passwords and configuration.
Why should I change the defaults? Leaving the default passwords on network devices (and software), especially ones that are Internet-facing, leaves a set of guessable credentials for an attacker to find and exploit. Even for internal devices with no connection the public Internet, a malicious insider may find the device on the network, log in with default credentials, and make a mess of things from there. In short, you should change the defaults on all network devices and software, especially those that are Internet-facing, to protect your network from intrusion. It's a simple step you can take, but one that is well worth it.
Tip 10: Create a Culture of Security
The previous tips all share something in common: it is not enough to implement a security program with technical controls alone. Humans are an important part of the security environment; they are often the actors that can take actions that make or break a security program. Creating a culture of security in your organization will go a long way toward making users aware of the risks of browsing the web, clicking links, and otherwise operating in a secure computing environment. Ultimately, a culture of security protects you, your organization, your customers, and the humans in your organization, both personally and professionally.
How you create a culture of security will depend on your specific organization, its tendencies, and existing cultural dynamics. From my perspective, creating a security culture begins at an executive leadership level with a commitment to integrating secure practices throughout the organization. You can find specific tips for creating a security culture from different technology publications. Ultimately, security belongs to everyone in your organization and the implementation of a security culture will come down to the nuances of your organization.
Summary
Security is a team effort, and it cannot be accomplished with technical controls alone. For your business, it is important to have policies in place that ensure everyone understands their role in maintaining security. Beyond this, I have described 10 practical tips you can start employing today to make your network more secure. These tips include technical practices, organizational practices, personal practices, and monitoring practices that will help you create, scale, and maintain a robust security program.
Stay vigilant and always keep learning. Vulnerabilities can develop quickly and start getting exploited rapidly. It is your job to take care of the security fundamentals so you can be prepared for new vulnerabilities that develop. NetworkCalc is one tool you can add that will help you monitor your domain for security changes. Consider creating a free NetworkCalc account to monitor your domain and websites for security changes - it's free to get started and will help ensure the security of your environment.